Ransomware attacks continued to wreak havoc on organizations across the world in 2022. According to the latest IBM’s Cost of a Data Breach report, the average ransomware attack cost reached USD 4.54M and took 49 days longer to identify and contain than the previous year. Following on from the infamous DarkSide and REvil ransomware gangs that were respectively responsible for the devastating attacks on the Colonial Pipeline and Kaseya in 2021, a new ransomware group has seen its stock skyrocket over the past year – BlackCat.
BlackCat was first discovered in November 2021 by researchers from the MalwareHunterTeam. Also known as AlphaVM, AlphaV, or ALPHV, the BlackCat ransomware group operates using the burgeoning Ransomware-as-a-Service (RaaS) model. BlackCat is the ransomware operator in this model, providing their ransomware kit to affiliates to launch their attacks. This means that BlackCat attacks will vary from affiliate to affiliate, especially in terms of initial entry.

(Source: MalwareHunterTeam)
BlackCat ransomware attacks have proven to be especially effective due to their unconventional programming and operating model. These include the first major professional ransomware written in the Rust programming language, substantially higher payouts to its affiliates, and leaking victim information on the public internet instead of just on the dark web.
The History of BlackCat Ransomware and Publicly Known Attacks
BlackCat ransomware was first discovered in November 2021 by researchers from the MalwareHunterTeam.
On 19 April 2022, the Federal Bureau of Investigation (FBI) Cyber Division published a Flash report detailing BlackCat’s indicators of compromise (IOCs). The report also observes that “many developers and money launderers for BlackCat/ALPHV are linked to Darkside/Blackmatter, indicating they have extensive networks and experience with ransomware operations.” These links have fueled speculation in the security circle that BlackCat is the rebranding of the two now-defunct ransomware groups.
Since its emergence, BlackCat has gained notoriety in a short space of a year after making headline after headline for several high-profile attacks. These include energy, manufacturing, construction, retail, technology, and finance organizations, with victims spread around the globe. The following are a few publicly known attacks perpetrated by BlackCat ransomware.
Examples of BlackCat Ransomware Attacks
Moncler: Italian luxury fashion brand Moncler suffered a BlackCat attack in December 2021, making it one of the first victims of the new ransomware strain. The fashion brand released a statement on 23 December informing that it had “detected a malware attack to its IT systems” and that “the company's security systems have immediately identified the attack, allowing the IT department to take all necessary actions to stop the spread.” On 30 December, Moncler released another statement, declaring that “unauthorized access to personal data has been detected.” On 18 January 2022, Bleeping Computer reported that Moncler’s stolen data appeared on BlackCat’s Tor leak site after refusing to pay the USD 3M ransom demand. Moncler confirmed that the stolen data includes information related to its employees, former employees, suppliers, consultants, business partners, and customers.
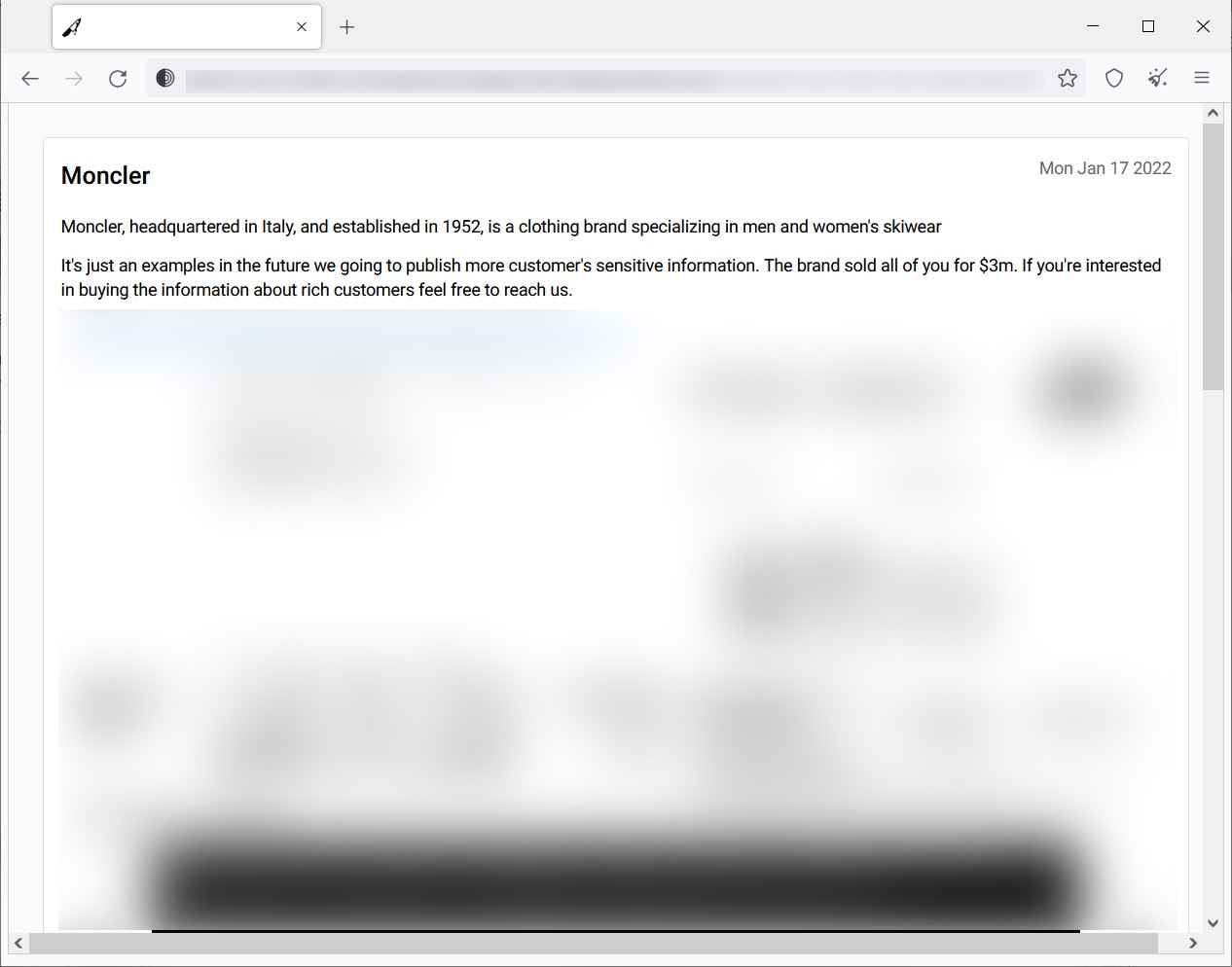
Moncler data leak page on ALPHV Tor site (Source: Bleeping Computer)
Oiltanking & Mabanaft: On 1 February 2022, the German business newspaper Handelsblatt reported that Oiltanking and Mabanaft, two subsidiaries of Hamburg-based logistics conglomerate Marquard & Bahls, have become the victims of hackers. The attack on Oiltanking – one of the largest independent tank storage providers for petroleum products, chemicals, and gases worldwide – caused chaos in Germany’s fuel distribution network. All of Oiltanking's loading and unloading systems were paralyzed, which resulted in 233 gas stations across Germany having to run some processes manually. At the same time, customers like Royal Dutch Shell were forced to reroute to different supply depots. According to another report by Handelsblatt on February 2022, an internal management report by the Federal Office for Information Security (BSI) revealed that BlackCat was responsible for the attack.
Empresas Públicas de Medellín: Empresas Públicas de Medellín (EPM) is one of Columbia's largest utility companies, providing energy, water, and gas to 123 municipalities. On 13 December 2022, the company disclosed to local media that it had suffered a cyber-attack. While the provision of energy, water, and gas was not affected, the attack took down the company’s IT infrastructure and online service, including online transaction platforms, and forced employees to work from home. After an investigation, the prosecutor's office confirmed that EPM had suffered a ransomware attack, while Bleeping Computer later learned that BlackCat was the perpetrator. It remains unclear how much data was stolen in the attack. However, what appears to be BlackCat’s data exfiltration server used for the attack shows a little over 40 devices listed on the index page.
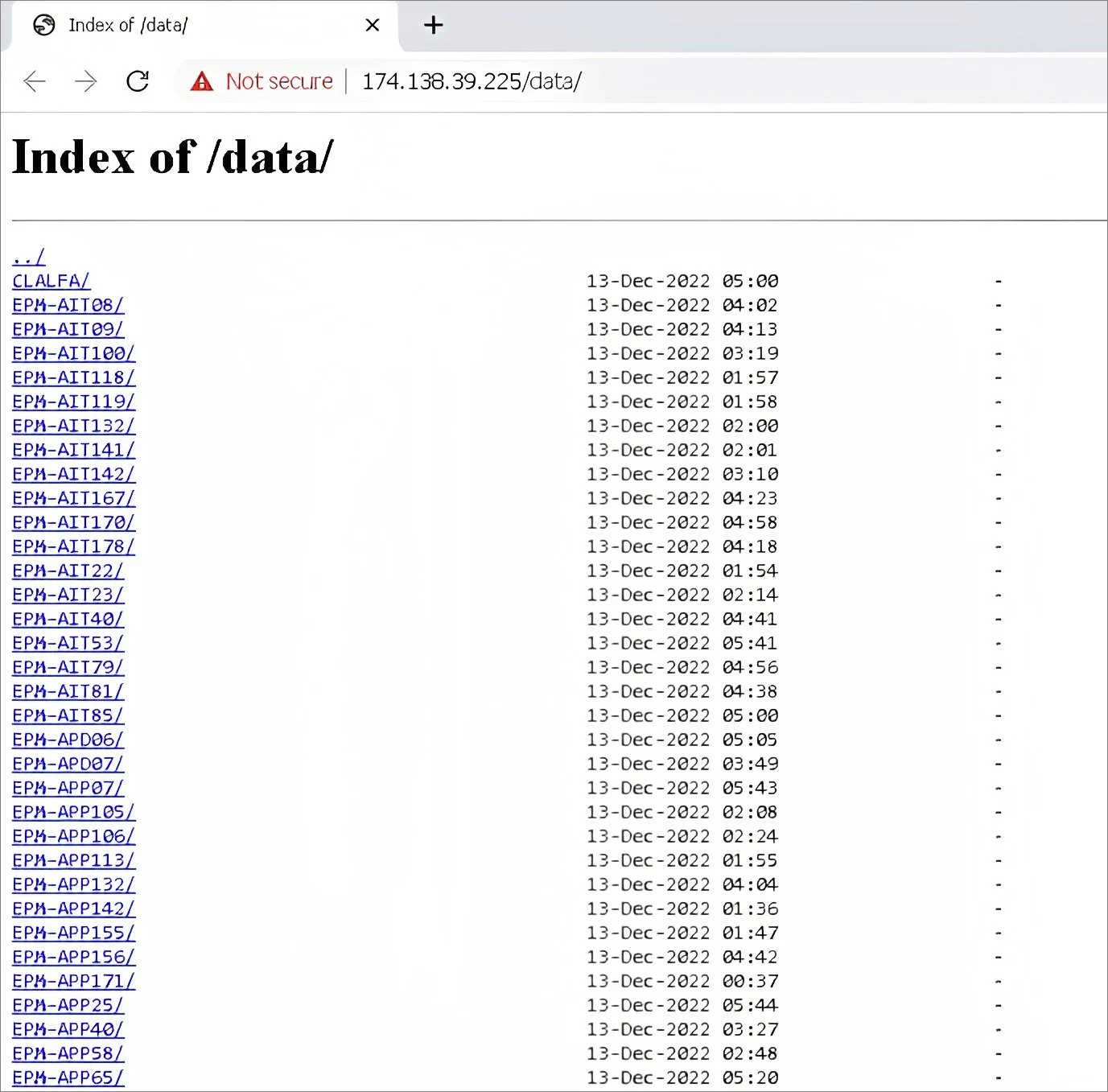
BlackCat Data Exfiltration Server (Source: Bleeping Computer)
Other publicly known attacks include:
- The Austrian federal state of Carinthia
- Gestore dei Servizi Energetici (GSE) SpA – Italy's energy agency
- Creos Luxembourg S.A. – A Luxembourgish natural gas pipeline and electricity network operator
- Swissport International Ltd. – A Swiss aviation services company providing airport ground, lounge hospitality, and cargo handling services.
What Makes BlackCat Ransomware Different
An unorthodox programming language and operating model, among other advanced tactics, techniques, and procedures (TTP), have seen BlackCat dubbed “the most sophisticated ransomware of the year.” The following section will examine what makes BlackCat unique from other ransomware strains and RaaS operators.
- Written in Rust
BlackCat is the first major professional ransomware written in Rust to launch attacks in the wild. Rust is a modern, cross-platform language compatible with various operating systems, including Windows, Linux, and even VMware instances. This allows affiliates to easily customize the BlackCat ransomware to the target environment to maximize the scope of file encryption. By writing the ransomware program in a modern language, BlackCat also improves the ransomware’s ability to evade security detection. This is especially true for organizations still using conventional security solutions not equipped to analyze and parse binaries written in such languages. Moreover, using a modern language also makes it more difficult for defenders to reverse engineer the ransomware to improve their understanding and defense against it.

- Higher Payout to Affiliates
BlackCat offers substantially higher payouts to its affiliates for successful attacks. BlackCat payouts reach as high as 90% of the received ransom as opposed to around the 70% that most RaaS operators pay. The high payout policy has contributed to BlackCat’s rapid rise and expansion in a highly competitive industry. By offering a higher payout, BlackCat can recruit affiliates through word of mouth rather than spending on advertising campaigns. This does not bode well for organizations as it incentivizes more threat actors to participate in ransomware attacks.
- Public Leak Site
Ransomware gangs typically publish the stolen data of victims unwilling to pay the ransom on their data leak sites. Historically, leak sites are only accessible on the dark web by victims, cybercriminals, and security researchers. However, BlackCat took the unprecedented step of creating the first data leak site on the public internet, accessible by everyone. This tactic takes double extortion to a new level as customers, shareholders, and other stakeholders will be loath to publicly make their information available and pressure the organization to pay up. On 1 January 2023, it was reported that BlackCat even cloned the website of a victim – an undisclosed financial services company – to use as the public leak site of its stolen data.
Defend against Ransomware with ForeNova
The uniqueness of BlackCat ransomware makes it a truly formidable threat. Its substantial payouts will no doubt incentivize more affiliates to sign up, putting organizations at large at risk of being on the end of one of their attacks. It is imperative for organizations, large and small, private and public, to upgrade their ransomware protection to safeguard their systems and prevent significant losses and impact.
ForeNova is here to help.
ForeNova is a specialist vendor of Network Detection and Response (NDR) technology. Our signature NDR solution, NovaCommand, provides security administrators with complete visibility of threats residing in the network. Using anomaly-based detection powered by artificial intelligence and machine learning, NovaCommand is equipped to detect and provide context into inconspicuous deviations in network behavior, allowing security operators to investigate and respond to signs of malicious activity before attackers can execute their ransomware.
An essential component of our Ransomware Detection and Response solution, NovaCommand is the only complete, holistic security solution to prevent and mitigate ransomware attacks in real-time.
- Block every step in the ransomware kill chain
- Direct integration between firewall and endpoint agents without using TI or management console as a go-between
- Block command & control communications and lateral propagation based on direct endpoint input
- Verify endpoint infection based on command & control communications
Organizations that wish to get protected against ransomware but cannot invest in the technology and personnel can leverage ForeNova’s Managed Detection and Response service. NovaMDR is an affordable subscription-based service where we provide the technology and expertise to protect your business. With round-the-clock threat detection and response from our 24/7 security operations center, customers can gain peace of mind from professional ransomware protection and dedicate their resources to growing the business.



.svg)
.svg)








