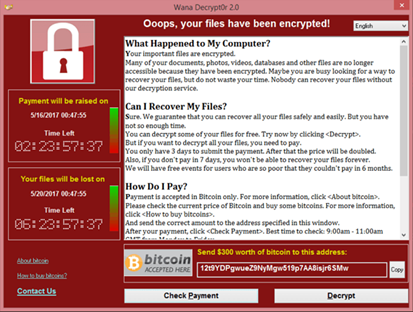
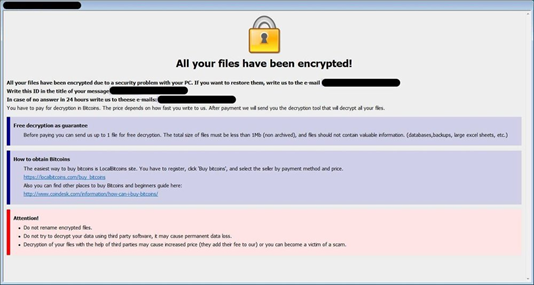
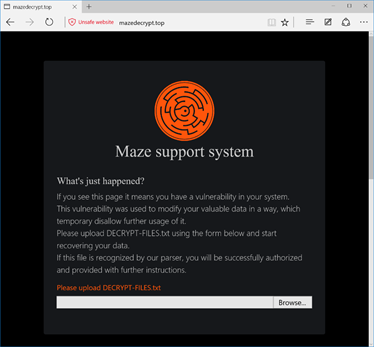
-
Managed Detection and Response with NovaMDR
NovaMDR leverages leading-edge security technology and world-class security experts
Forenova Compliance Guide
We are committed to supporting our customers in their journey towards regulatory compliance.
-
Detect and protect.
ForeNova represents a new way for companies to put an end to relentless, and often undetected, cyber threats coming from every direction. With ForeNova’s unified command center, businesses can detect threats that are already inside their network, and previously unknown.

-
Blog
Cybersecurity Essentials