Nowadays, the cybersecurity experts, not the knights in shining armor, are responsible for protecting us. The chief information security officers (CISOs) defend our companies' virtual entrances and are thus unsung heroes in the fight against unseen enemies.
Investigate where SIEM is at the moment, what developments are on the horizon, and the best practices that each CISO should follow. Find out how companies worldwide are getting ready for the next big thing in cybersecurity by shoring up their defenses, reflecting on and gaining wisdom from past mistakes, and anticipating what lies ahead.
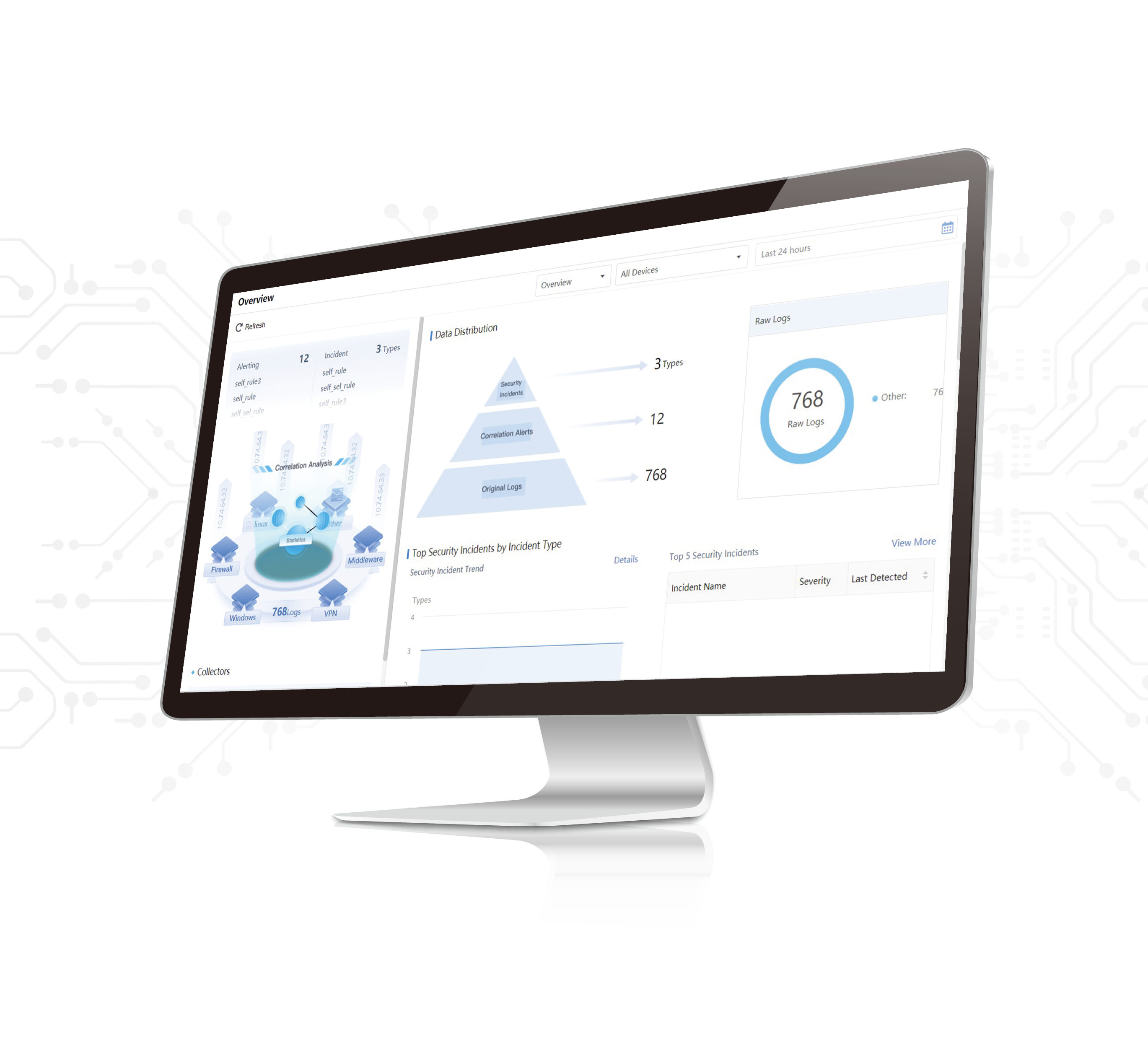
What is SIEM?
SIEM stands for security information and event management. It's a critical tool for modern
cybersecurity, but it's often misunderstood and underutilized.
SIEM can be useful in helping organizations detect and respond to security threats quickly
and effectively. SIEM solutions collect and analyze data across an organization's IT
infrastructure, providing a single view of security activity. This allows organizations to identify
suspicious activity, investigate incidents, and take corrective action before damage is done.
Imagine a world without SIEM
Organizations would be flying blind, unable to see the threats that are lurking in their networks. Hackers would have free rein, stealing data and disrupting operations. Businesses would be at the mercy of cybercriminals.
SIEM is the secret weapon of the modern CISO. It's the tool that gives you the visibility you need to see the threats that are lurking in your network and the intelligence you need to respond to them quickly and effectively. However, SIEM is also a complex and expensive technology that can be difficult to implement and manage.
The Current State of SIEM

Opening the Cybersecurity Atlas
SIEM provides a foundation for safeguarding our most valuable assets - data, privacy, and trust. But to understand where we're headed, we must first map the terrain we currently occupy.
The Digital Sentry
Let’s imagine that your organization is a fortress built not of stone and mortar but of bytes and algorithms. A sentry stands at its gate, and their role is paramount.
SIEM is the vigilant guardian, keeping watch over the vast expanse of your digital kingdom. It sees the footprints of intruders, hears the whispers of malware, and senses the tremors of data breaches. It is the eyes, ears, and heart of your cybersecurity strategy.
The Evolution of SIEM
SIEM didn't rise to its current stature overnight. It has evolved, adapted, and grown. It was born out of necessity, as organizations faced the growing challenge of managing an overwhelming amount of security data. It started as a log management tool, collating logs and events from various sources for analysis.
Over time, SIEM has integrated advanced capabilities such as real-time monitoring, threat detection, and incident response. It's no longer a passive observer but an active participant in the ongoing battle against cyber threats.
SIEM Benefits and Challenges
There are pros and cons to using SIEM, just as there are to any other program.
Among its many advantages is the fact that it allows you to keep tabs on your digital domain in real-time, which is great for spotting threats early and responding quickly. You can keep ahead of attackers with its ability to correlate events and produce alarms.

Benefits of using SIEM Solutions
- Improved visibility into your security posture
- Faster threat detection and response
- Reduced workload for security teams
- Helps meet compliance requirements
Challenges of using SIEM Solutions
- The volume and complexity of security data can be overwhelming
- False positives can lead to alert fatigue
- SIEM solutions can be expensive and complex to implement and manage
The SIEM Misconceptions
Before we dive deeper, it's essential to debunk some common misconceptions about SIEM.
- SIEM is a silver bullet that can solve all of your security problems.
- SIEM is only for large enterprises
- SIEM is difficult to implement and manage
- SIEM is too expensive and complex for small and medium-sized businesses
The Latest SIEM Trends
SIEM technology is constantly evolving, and new trends are always emerging. The cloud-based SIEM market is expected to grow from $4.5 billion in 2021 to $9.82 Billion by 2027.
Here are some of the latest SIEM trends that you should be aware of:
The rise of cloud-based SIEM solutions
Cloud-based SIEM solutions are becoming increasingly popular as they offer a number of advantages over
on-premises SIEM solutions, such as scalability, affordability, and ease of deployment.
The use of artificial intelligence and machine learning (AI/ML) in SIEM
According to a report by Gartner, 80% of SIEM vendors plan to integrate AI/ML into their solutions by 2025. AI/ML is being used in SIEM solutions to improve their ability to detect and respond to security threats. For example, AI/ML can be used to identify anomalous behavior and patterns in security data, which can help organizations identify and respond to threats more quickly and accurately.
The convergence of SIEM and security orchestration, automation, and response (SOAR)
SIEM and SOAR are two complementary technologies increasingly converging into single platforms.
This convergence allows organizations to automate their response to security incidents, which can help reduce the time it takes to respond to threats and reduce the workload on security teams.
Automation
Automation is playing an increasingly important role in SIEM. SIEM solutions can be automated for various tasks, such as data collection, analysis, and reporting. This can help organizations to save time and resources and to improve the efficiency and effectiveness of their security operations.
Behavior analytics
Behavior analytics is a new breed of SIEM technology that uses AI/ML to analyze user behavior and identify
anomalies that could indicate a security threat. Behavior analytics can help organizations detect threats that would be difficult to find using traditional SIEM rules and signatures.
Threat intelligence sharing
Threat intelligence sharing is the practice of sharing information about security threats between organizations. This can help organizations to stay up-to-date on the latest threats and to develop more effective defenses against them.
How to Improve Your Security Posture on a Low Budget
We understand the challenges you face as IT security managers and CISOs:
Daily battles include limited budgets, increasing threat complexity, and inadequate staff resources.
Do You Really Need a Full SIEM Implementation?
|
Factor
|
Full SIEM Implementation
|
SIEM Light Solution
|
|
Scope of Security Features
|
Offers comprehensive features, including advanced threat detection, incident response, and detailed analysis.
|
Provides essential security features, such as log management, basic threat detection, and compliance reporting.
|
|
Budget Considerations
|
Typically comes with a higher initial investment and ongoing costs, including hardware, licensing, and maintenance.
|
Cost-effective option with lower upfront and ongoing costs, making it suitable for organizations with budget constraints.
|
|
Resource Demands
|
Requires a dedicated team or experts to manage and maximize its advanced capabilities.
|
Easier to deploy and maintain, requiring fewer resources and expertise, making it suitable for lean IT staff.
|
|
Regulatory Compliance
|
Well-suited for organizations subject to strict compliance requirements, providing comprehensive log management and reporting.
|
Sufficient for meeting basic compliance needs
|
|
Data Volume Handling
|
Capable of efficiently handling and analyzing a significant volume of log and event data.
|
Suitable for organizations with moderate data
|
|
Deployment Speed
|
Typically involves a longer implementation process due to the complexity of the solution.
|
Allows for faster deployment, making it a good choice for organizations seeking rapid security enhancement.
|
|
Scalability
|
Offers scalability to accommodate the growth of an organization's security needs.
|
Some SIEM Light solutions offer scalability, allowing organizations to start small and expand as needed.
|
|
Ideal Use Cases
|
Large enterprises with complex security needs and dedicated security teams.
|
Small to medium-sized organizations, those with budget constraints, lean IT staff, and businesses seeking essential security features.
|
|
Flexibility
|
Provides extensive customization and flexibility in adapting to specific security requirements.
|
Offers core security features without the complexity, providing a streamlined and efficient approach.
|
The choice between a full SIEM implementation and an SIEM Light solution depends on factors such as an organization's size, budget, regulatory requirements, available expertise, and specific security needs. Careful consideration of these factors will help select the most appropriate SIEM solution for your organization.
Proving ROI and Making a Case for a SIEM Light
To gain the support of the CFO and CEO, IT security managers and CISOs must prove the ROI for an SIEM solution.

Cost Reduction Through Efficiency
- Demonstrate how a SIEM Light solution minimizes costs.
- Emphasize savings on hardware, software, and maintenance.
- Show the financial benefits of simplified management.
Example: Implementing SIEM can lead to a 30% reduction in the IT security budget. This reduction is achieved through the elimination of manual log analysis tasks and streamlined incident response, reducing overtime costs for IT staff.
Improved Threat Detection and Response
- Showcase how SIEM Light enhances threat detection and response.
- Use real-world examples to illustrate potential financial losses prevented.
- Highlight the cost-effectiveness of quicker incident resolution.
Example: SIEM detects a suspicious pattern of login attempts, leading to the early identification of a potential breach. Quick response prevents data loss and saves an estimated $100,000 in remediation costs.
Compliance Efficiency
- Explain how SIEM Light streamlines compliance efforts.
- Emphasize how automation reduces the time and effort required for compliance tasks.
- Provide examples of potential compliance fines avoided.
Example: SIEM automates compliance reporting, reducing the time spent on manual data collection by 50%. This streamlined process leads to an estimated cost saving of $40,000 annually in compliance-related efforts.
Resource Optimization
- Demonstrate how SIEM Light optimizes staff resources.
- Show that IT staff can focus on higher-impact tasks, enhancing overall efficiency.
- Illustrate cost savings by reducing the need for additional security staff.
Example: Implementing SIEM allows IT staff to focus on proactive security measures rather than reactive incident response. This shift in focus increases productivity by at least 25%, enhancing the organization's overall security posture.
Scalability and Future-Proofing
- Explain how SIEM Light allows for scalability as the organization grows.
- Highlight that the solution adapts to changing security needs without a proportional cost increase.
- Discuss the long-term cost-effectiveness of a flexible SIEM solution.
Example: As the organizations expand, the SIEM solution seamlessly scales to accommodate the growing security needs without incurring additional licensing costs. This flexibility saves organizations an estimated $60,000 in licensing fees.
Business Continuity Assurance
- Convey the financial impact of ensuring business continuity.
- Explain that SIEM Light helps prevent downtime and potential financial losses.
- Use data breach examples to underscore the cost of reputational damage.
Example: During a DDoS attack, SIEM identifies the threat and triggers automated countermeasures, ensuring uninterrupted service. This prevented potential revenue loss and protected the organization's reputation.
Demonstrated Value through Metrics
- Establish Key Performance Indicators (KPIs) and metrics to track the impact of SIEM Light.
- Provide regular reports that show improvements in security, compliance, and cost savings.
- Link SIEM Light's performance to the organization's overall financial well-being.
Example: Quarterly reports can show that SIEM reduces the mean time to detect and respond to incidents by 40%, resulting in an estimated annual savings of $150,000 in potential breach-related costs.
Other Ways To Improve Your Security Posture on a Tight Budget
When resources are tight, prioritize risk management. Identify the most critical assets and potential threats. Allocate your limited resources to safeguard what matters most, making the most of your budget and staff.
Try Open Source SIEM Solutions
Consider open-source SIEM solutions. They offer cost-effective alternatives without compromising security. Many open-source options are community-supported and can be tailored to your specific needs.
Cloud-Based SIEM
Explore cloud-based SIEM solutions. They reduce the need for on-site hardware and staff resources. With cloud SIEM, you can scale your security efforts as needed and pay only for what you use.
Managed SIEM Services
Consider outsourcing SIEM management to a third-party provider. Managed SIEM services can be more cost-effective than building an in-house team, providing 24/7 monitoring and incident response.
Resource-Efficient Data Management
Maximize the value of your data by focusing on the essentials. Collect and store only the data that's critical for your security needs. This reduces storage costs and eases the workload on your staff.
Orchestration & Automation
Implement orchestration and automation to make the most of your limited staff. Automate routine tasks like log analysis and incident triage, freeing your team to focus on high-impact security issues.
Lean Incident Response Plan
Develop a lean and agile incident response plan. Prioritize the most likely and high-impact scenarios. Your plan should be a living document that evolves based on real-world experiences.
These practices are the building blocks for a resilient cybersecurity strategy, even when you're working with minimal resources.
They're not just theoretical solutions but actionable steps that IT security managers and CISOs can implement today to enhance their organization's security posture.
Using SIEM To Prove Compliance
Using SIEM systems is becoming the key to demonstrating compliance as the digital landscape becomes more regulated.
Adhering to industry-specific mandates and regulatory standards like the Network and Information Systems Directive (NIS2) requires careful log and event management. A key component to achieving compliance in these areas is SIEM solutions.
SIEM systems produce thorough reports and alarms that provide businesses with the verifiable documentation needed to prove compliance in regulatory audits. The foundation of regulatory compliance is this trail of evidence.
The Burden of an Expensive Full SIEM Solution
While the allure of traditional SIEM solutions is undeniable, they often come with a heavy price tag and operational complexities. The burden of a full SIEM solution can be overwhelming for organizations, especially when compliance is at stake.
Investing in a full-scale SIEM solution demands a substantial financial commitment. Organizations, especially those operating on tight budgets, may find allocating resources to procure, deploy, and maintain such systems challenging.
Traditional SIEM solutions are renowned for their complexity. The learning curve for administrators and security teams can be steep, delaying deployment and potentially leaving security gaps in the interim.
Managing a full SIEM solution requires a dedicated team of experts. The resource-intensive nature of these solutions can strain an organization's workforce, diverting valuable human resources from other critical security functions.
NovaMDR includes SIEM Light
NovaMDR seamlessly integrates SIEM Light functionality, addressing the challenges of regulatory compliance.
NovaMDR offers a cost-effective solution, alleviating the financial strain of full-scale SIEM implementations. It enables organizations to achieve regulatory compliance without breaking the bank.
NovaMDR's user-friendly interface and simplified design ensure that organizations can quickly adopt and harness the power of SIEM Light without grappling with a steep learning curve.
It streamlines resource management by reducing the need for a large team of experts to oversee complex SIEM implementations, allowing organizations to channel their human resources more efficiently and ensuring regulatory compliance without overextending their workforce.
Real-World Examples of How SIEM Light Solutions Can Help CISOs
SIEM light solutions offer a more affordable and accessible alternative, providing the core capabilities of log management, threat detection, and incident response without the overhead and maintenance of a full-fledged SIEM solution.
By leveraging cloud-native technologies, artificial intelligence, and threat intelligence, SIEM light solutions can help CISOs achieve effective security outcomes without compromising on performance, scalability, or usability.
SIEM in Healthcare
Protecting sensitive patient data: SIEM light solutions can help CISOs in the healthcare industry protect their sensitive patient data from cyber threats by:
- Monitoring EHRs, medical devices, and other systems for suspicious activity, such as unauthorized access or changes to patient records.
- Detecting known and unknown threats, such as malware, insider threats, and ransomware.
- Automating incident response to contain and remediate breaches quickly.
- For example, a SIEM light solution can help a hospital chain detect and respond to a ransomware attack in real-time, preventing the attackers from encrypting patient data and minimizing disruption to patient care.
SIEM in Retail
Securing customer data and payment information: SIEM light solutions can help CISOs in the retail industry secure their customer data and payment information from cyber threats by:
- Monitoring POS systems, e-commerce platforms, and inventory management systems for suspicious activity, such as unauthorized access to customer accounts or fraudulent transactions.
- Detecting known and unknown threats, such as skimming attacks, credential stuffing, and supply chain attacks.
- Automating incident response to contain and remediate breaches quickly.
- Manufacturing/Automotive
Protecting industrial control systems: SIEM light solutions can help CISOs in the manufacturing industry protect their industrial control systems from cyber threats by:
- Detecting known and unknown threats, such as malware, denial-of-service attacks, and sabotage.
- Automating incident response to contain and remediate breaches quickly.
- Manufacturers could detect and respond to a malware attack that was targeting their industrial control systems. The SIEM solution identified suspicious activity on the manufacturer's network and alerted security analysts, who were able to isolate the infected systems and prevent the malware from spreading.
A Full Year of Advanced Cybersecurity for Less than the Cost of One Full-Time Employee
+ Get Complete Access to an Entire Team of Cybersecurity Professionals
Comprehensive Cybersecurity at a Fraction of In-House Costs
ForeNova’s NovaMDR services offer a year of robust cybersecurity protection that is more cost-effective than hiring a full-time cybersecurity expert. With our service, you gain access to a whole team of seasoned cybersecurity professionals for less than the cost of a single full-time position. This cost efficiency ensures your organization's security budget is optimized without compromising on the level of protection.
Integrated SIEM Light – Advanced Technology Made Simple
Our MDR services include an integrated Lightweight SIEM (Security Information and Event Management) system. This technology enhances your cybersecurity posture by providing real-time monitoring and response capabilities. It simplifies the complexity typically associated with traditional SIEM systems, making it more accessible and less resource-intensive for your IT team.
24/7 Expert Monitoring and Rapid Response
ForeNova’s NovaMDR service guarantees around-the-clock monitoring of your network and endpoints. Our experts are poised to detect and respond to threats in real-time. With a time-to-notify of under 10 minutes following a critical incident, our team ensures rapid mitigation and resolution, significantly reducing potential damage and downtime.
Leverage Human-Machine Intelligence
The service blends cutting-edge AI and machine learning technologies with human expertise, providing a balanced approach to threat detection and response. This synergy ensures that nuanced threats, which automated systems might overlook, are identified and addressed promptly.
Seamless Integration with Your Existing Infrastructure
ForeNova’s NovaMDR service is designed to integrate your existing IT security infrastructure fully. This adaptability means the transition to using our services is smooth, with minimal disruption to your current operations.
See for yourself: https://www.forenova.com/managed-detection-and-response-mdr/