Get Your Attack
Surface Blueprint
Stop ransomware before the point of no return with a complete view of your network environment
Cyber criminals look for the easiest targets with the biggest potential gains.
The most alarming part is that you might already be under attack and not even know it.

62%
of threats are missed due to false positives.

65%
of cyberattacks go undetected.
Ransomware is
Rampant
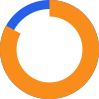
of IT leaders believe complexity presents the biggest risk for a ransomware attack.
Cyber criminals operate as professional and legitimate enterprises, preying on the increasing complexity of the IT landscape.
Organisations Are
Unprepared

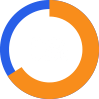
of CISOs do not believe their organisation is prepared to handle a cyberattack.
The severe shortage of cybersecurity skills has made it difficult for organisations to recover quickly.
The Impact Can Be
Devastating

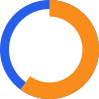
of small to midsize businesses close within six months of a cyberattack.
Ransomware will cost victims more than $265k annually by 2031 with a new attack occurring every 2 seconds.
Select an industry to expose your attack surface
Manufacturing
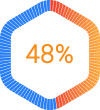
of manufacturing companies have been victim to a cybersecurity attack.
The average ransomware payout in the industry is $172k per incident and is on the rise.

Healthcare

of healthcare organisations have experienced a security breach.
Ransomware attacks cost healthcare organisations $21 billion in lawsuits, ransom paid, lost revenue, fees to rebuild lost data, and more.
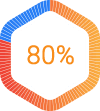
Retail

of retail organisations have been the victim of a ransomware attack.
The average cost of a retail ransomware attack, including downtime, labour, ransom paid, device and network costs, is $1.97M per event.

what make a manufacturing targets attractive to cybercriminals?

Valuable intellectual property including new technologies or designs have a high resale value for cybercriminals.

With strict output schedules, manufacturers are likely to pay the ransom to keep production moving.
A wide network of third-party vendors (including suppliers) gives cybercriminals easy access to additional victims in the ransom demand chain.
manufacturing vulnerabilities
IoT
of manufacturers have initiated the adoption of loT in their operations.
Legacy manufacturing networks were generally not designed with the threat of a ransomware attack therefore connected lol devices often present an easy path of entry for cybercriminals.

SUPPLY CHAIN
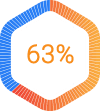
of security breaches are caused by third-party providers including vendors and suppliers.
The supply chain is a lucrative target, as third-party suppliers require access to critical data and often accept weaker security processes, making data vulnerable.

INSIDER THREATS
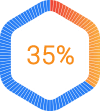
of ransomware attacks on manufacturers are due to human error or intentional acts from persons with network access.
Employees, including machine operators,office personnel,and delivery drivers, have access to critical systems and company data.


ForeNova shines the light on unknown threats
Only ForeNova can show you the blueprint that ransomware attackers
use to find your weaknesses. Armed with these insights, you can move quickly and
confidently to detect and respond to unknown threats.

Unprecedented
Visibility

Unified Command
Center

Network-Centric
Detection & Response
Fight back with your attack surface blueprint from ForeNova.
Our NDR experts will show you what cyber criminals see and how to respond with speed and accuracy.



