The reason why threat actors often find success in phishing is that they exploit the greatest vulnerability of all: human emotions. A phishing attack becomes successful only if the user falls for social engineering tricks. So, the trick is to be careful. Good awareness and experience can help you detect almost all types of phishing attacks. Here’s how:
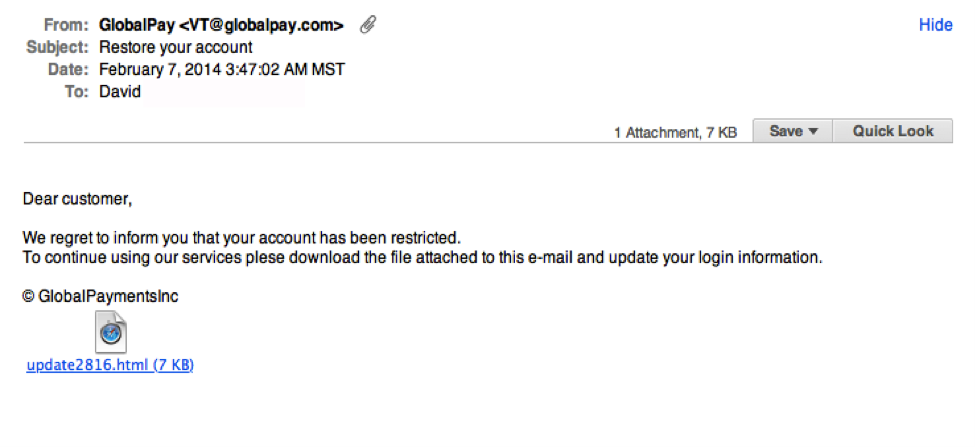
• See if the mail addresses you by name. Phishing emails mostly use generic salutations like ‘dear customer’ or ‘deal member’.
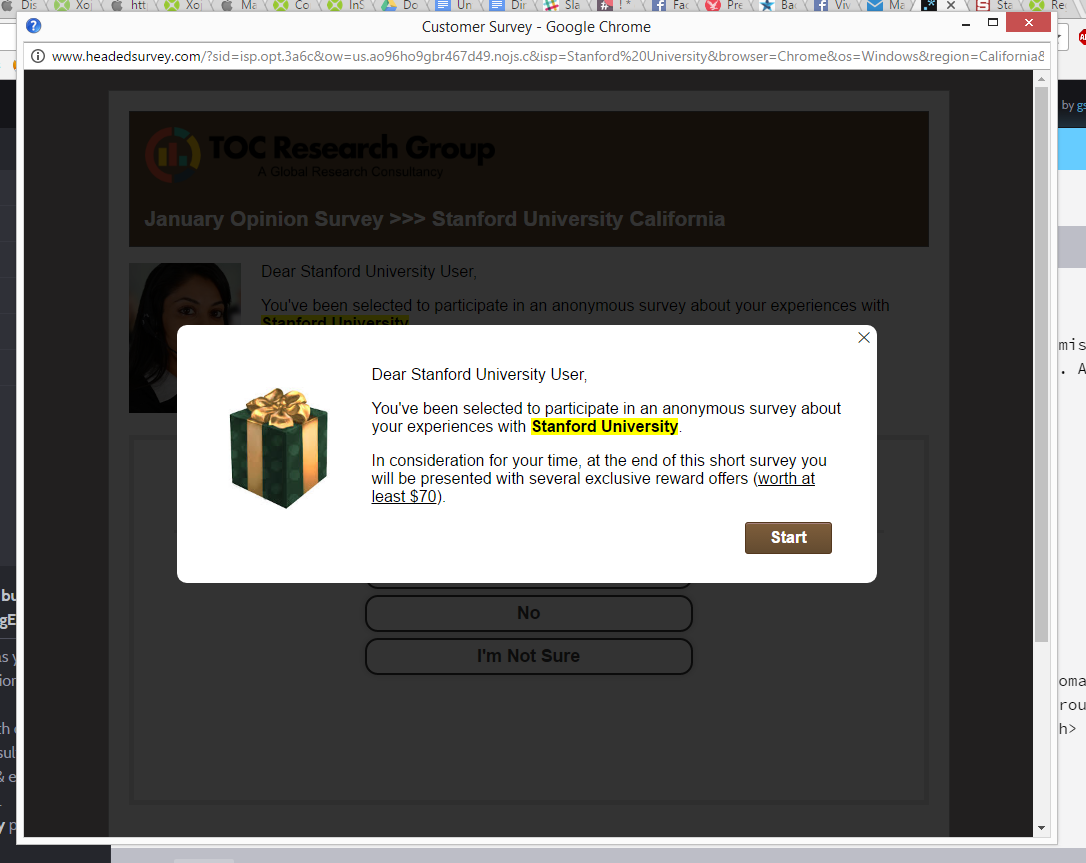
• Legitimate companies don’t request sensitive information via email, SMS, or calls. So, double-check if you see something like that.
• A mail from shopping@amzaon.com doesn’t mean it’s from Amazon. Why? Read the mail address again and check how ‘amazon.com’ is spelled. Attackers often use different variations of a legitimate brand to look less suspicious.
• Be alert when someone from your enterprise, especially your superior who doesn't contact you that often, suddenly starts messaging you. If they ask for any sensitive information via message, don’t hesitate to call them up in person to double-check.
• If anyone tries to reach out via social media claiming that they are from a particular company, check if their profiles are verified (blue tick). You can also contact customer support directly via phone or website to verify.
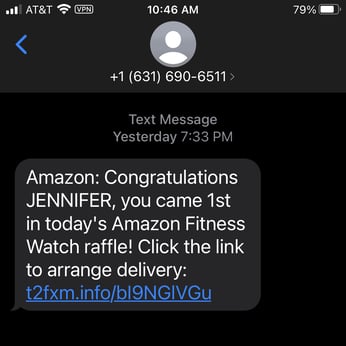
• It’s better to avoid short links altogether, no matter the source. You can’t see the domain or SSL on short URLs; so, it’s not safe to open such links, especially if they're embedded in an email or SMS.
• Phishing emails often have a large number of spelling mistakes. The way they use grammar is a bigger crime than the phishing attack itself. If you feel the language is somewhat off, it’s probably a phishing email.
• Educate employees, especially newbies and untrained, about phishing emails and also the dos and don'ts while using email, social media, and applications while on the enterprise network.
• Use a network detection and response (NDR) application for your enterprise to track any suspicious activity.