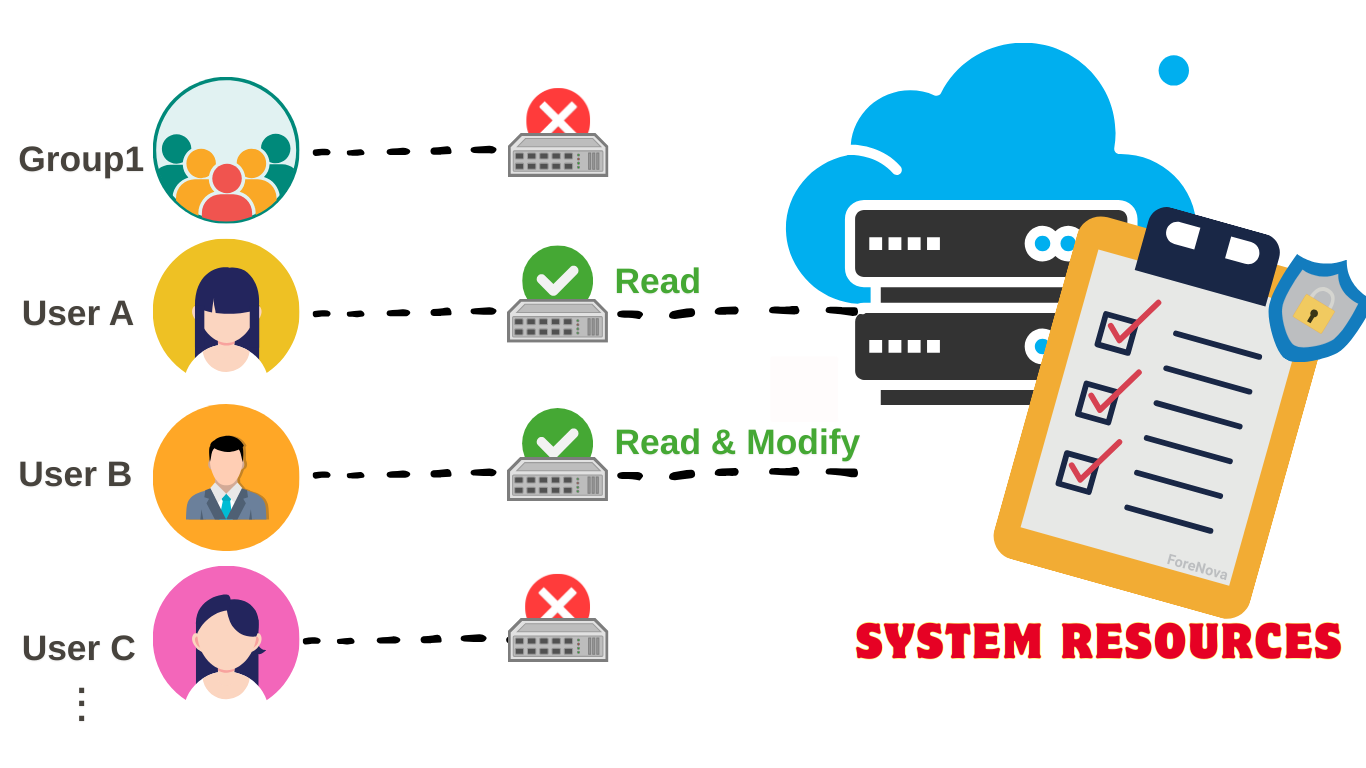
What is Access Control List (ACL)?
An Access Control List (ACL) is a security mechanism which is designed to determine which user or which system has the right to access a specific object or system resource, such as files, directories, network services and so on. As well as operations are allowed on given objects, including read, edit or execute. Thus, ACLs can be seen as a fundamental component of a robust security strategy.
Difference between Firewalls and Access Control Lists
Firewalls and ACLs are crucial components of a comprehensive network security strategy, with each playing an important role in securing the organization’s sensitive resources. The following are the main distinctions between firewalls and ACLs:
- Scope: Firewalls govern traffic flow at the network perimeter, whereas ACLs control access permissions within the network.
-
Detail Functions: ACLs primarily provide specific users with granular access control based on task level or job title with the creator’s settings to protect resources, whereas firewalls attempt to monitor and control incoming and outgoing network traffic based on predetermined security rules to ensure system security.
- Implementation: Firewalls are independent hardware or software programs that must be placed on the network. ACLs, on the other hand, are built into network interfaces and operating systems as well as configurable on some routers and switches.
Why do we need an Access Control List?
ACLs are specified sets of rules that are vital for sustaining the security and integrity of both network resources and local systems:
-
Enhanced Security
ACLs provide the ability to define and enforce specific access permissions for devices and users, enhancing security by reducing the risk of unauthorized access and potential breaches. In addition, detailed control not only includes the right to access but also what actions they can perform. This granularity adheres to the principle of least privilege and helps ensure that users can complete their tasks only with the permissions matching to their job position.
-
Ensure Compliance
Many industries, such as healthcare, finance, retail, telecommunications, automotive industry, etc., have regulatory requirements for controlling access and protecting customer data. With the implementation of ACLs, organizations can comply with these regulations by ensuring only specific users are granted access to or modify sensitive information.
-
Audit and Monitoring
With granular control, ACLs make it easier to monitor access to resources and track the record. You can log who access what and when, providing valuable information for audits and incident investigations.
-
Decrease Insider Threats
Organizations can mitigate the risk of insider threats by restricting access with ACLs to make sure that employees can only see what is relevant to their roles.
The Different Types of Access Control List
-
Standard ACL
Standard ACL is one of the most basic forms of ACLs, which are used mainly in network security to manage and filter network traffic by permitting or denying packets based solely on the source IP address. It can be implemented typically on network devices like routes or firewalls and can be applied to inbound or outbound traffic on an interface. It has a number between 1-99 and 1300-1999 on Cisco devices.
-
Extended ACL
Extended ACL is an ACL which provides more granular control over network traffic compared with standard ACLs, which are more useful for detailed traffic control and security measures. It allows you to filter traffic based on not just the source IP address but also the destination IP address, protocol, and protocol numbers. It is identifiable in Cisco routes by a number between 100 and 199 and 2000 to 2699.
-
Named ACL
Named ACL is more intuitive and flexible due to 2 reasons. It can be used as either Standard ACL or Extended ACL to offer the same capabilities for traffic filtering and access control. On the other side, it’s identified by using descriptive names instead of the other using only numbers, which makes them easier to manage, clarify and remember.
-
Dynamic ACL
Dynamic ACL, also known as ‘Lock-and-key ACL’, is an advanced type of ACL used in network security which enhances security by ensuring that access is granted only to verified users for a limited period. When the user successfully authenticates, a temporary rule will be added to the ACL to allow access. After the session has ended or the timeout period expires, the rule will be removed. Additionally, it’s useful for controlling remote user access and providing more granular security for organizations.
-
Reflexive ACLs
Reflexive ACL, also known as ‘IP session ACL’ or ‘Session filter’, is a dynamic ACL that is used commonly for measures in routing and switching environments in network security. It provides stateful inspection and control of IP traffic by allowing return traffic for established sessions while denying unsolicited incoming traffic. What’s more, with this type of ACL, organizations can track and filter traffic based on the state of active sessions.
The Components of an Access Control List
An ACL consists of the following several components central to its function:
- Sequence number: The sequence number identifies the ACL entry with a specific number.
- ACL name: The ACL name defines the ACL entry by using a specific name assigned to it instead of numbers. But in some cases, the router will allow use of both numbers and characters.
- Remark: On some routers, you can insert some comments to show more detailed descriptions.
- Statement: With a statement, you can permit or deny a source using a wildcard mask or address, which can dictate the system to examine a specific element of an IP address.
- Network protocol: The network protocol can be used to permit or deny certain networking protocols, such as IP, Internetwork Packet Exchange (IPX), Transmission Control Protocol (TCP), Internet Control Message Protocol (ICMP), User Datagram Protocol (UDP), and so on.
- Source or destination: The source or destination component defines the destination or source IP address as an address range or a single IP or allows all addresses.
- Log: There are devices that can maintain a log when they find ACL matches.
- Other criteria of advanced ACLs: Some more advanced ACLs give you the option to control traffic according to IP precedence, the type of service (ToS), or its priority as derived from its Differentiated Services Code Point (DSCP), which is a networking architecture that allows for the classification and management of traffic on a network.
Where do you place an Access Control List?
To ensure that users and systems are following the prescribed rules, an ACL might be installed on some routers or switches for monitoring incoming and outgoing network traffic. Besides, it can also be built into any various network interfaces and operating systems to manage and enforce security policies. Whether which methods, ACLs are a fundamental tool for preserving organizations’ security and integrity across both networked and local environments.
How to Implement an ACL on a Router?
If you’re looking to implement an ACL, ForeNova is on call to help you every step of the way. However, to correctly deploy ACL on your router, you must understand how traffic flows in and out. You define the rules from the perspective of the router’s interface. This differs from that of the networks. For example, if traffic enters a router, it exits a network; hence, the perspective has a significant impact on how the traffic’s path is depicted.
To work properly, an ACL must be added to the router’s interface. The router’s hardware executes the forwarding and routing decisions, making the process quicker.
While adding an ACL entry, enter the source address first and then the destination address. When supplied in this style, the router recognizes the entry and reads it. The source is where the traffic originates, which is located “outside” of the router. The destination is the location beyond the router where the data packets will finish up.
Linux ACL vs. Windows ACL
Linux ACL |
Windows ACL |
|
Type |
POSIX ACLs |
NTFS ACLs |
Permissions |
Read, Write, Execute |
Full Control, Modify, Read, Execute, List Folder Contents, Write |
Management |
Command Line |
GUI or Command Line |
Inheritance |
Limited support |
Strong support |
Integration |
Linux file system |
Windows operating system and Active Directory |
Linux ACL provides more flexible permission mechanisms for resources in the Linux file system compared to the traditional Unix file permission system. While Windows ACL is the security function in the Windows operating system that controls the permissions for access to sensitive files.
Although both aim to enhance the safeguard of the organization system, there are 4 points that are different and need to be pointed out:
- Detailed Permissions: Windows ACL provides a wider range of more granular permissions for users with not only Read, Write, and Execute but also Modify and Full Control.
- Interface Management: Linux mainly uses Command Line tools, while Windows manages through the Windows Explorer GUI or using command line tools.
- Inheritance: Compared to Linux, Windows has more robust inheritance features, which means the permission can be inherited from parent directories.
- System Integration: Windows ACLs are tightly integrated with both the Windows operating system and Active Directory (AD), which provides more centralized control in a networked environment compared to the decentralized nature of Linux file systems.







