How To Create an Engaging Cybersecurity Capture The Flag (CTF) Event
What is a Capture the Flag Event?
Capture The Flag (CTF) events are competitive cybersecurity challenges that simulate real-world scenarios, testing participants’ skills in various areas of information security.
These events typically involve solving puzzles, exploiting vulnerabilities, and defending systems, all within a controlled environment.
CTFs can range from small, local competitions to large-scale international events, each offering unique learning opportunities and challenges.
Who are CTFs for?
CTFs attract a wide range of participants from the cybersecurity community:
- Cybersecurity professionals for sharpening skills and staying current with emerging threats and defense techniques.
- Aspiring cybersecurity experts can gain practical experience and build their portfolios.
- Hobbyists and self-taught individuals can test their skills and learn from peers.
- Organizations use CTFs for team building, skill assessment, and talent recruitment.
- Security researchers can challenge themselves with cutting-edge problems and share knowledge.
Why are CTFs important?
- Skill Development
CTFs provide hands-on experience in real-world scenarios, allowing participants to apply theoretical knowledge in practical situations.
- Networking
These events bring together like-minded individuals, fostering community building and professional connections.
- Innovation
The competitive nature of CTFs encourages creative problem-solving and the development of new security techniques.
- Talent Identification
Companies can identify skilled individuals for potential recruitment, observing how they perform under pressure.
- Continuous Learning
The dynamic nature of CTFs ensures participants stay updated with the latest security trends, tools, and vulnerabilities.
- Security Awareness
CTFs help raise awareness about cybersecurity issues among participants and the broader tech community.
- Career Advancement
Success in high-profile CTFs can boost a participant’s reputation and career prospects in the cybersecurity field.
Step-by-Step Guide to Creating a Successful CTF Event
Step 1: Choose the Right CTF Format
Choosing the right format is key to the success of your CTF event. Each format brings its own strengths and works best for different audiences and learning goals.
Let’s find the perfect fit for your event:
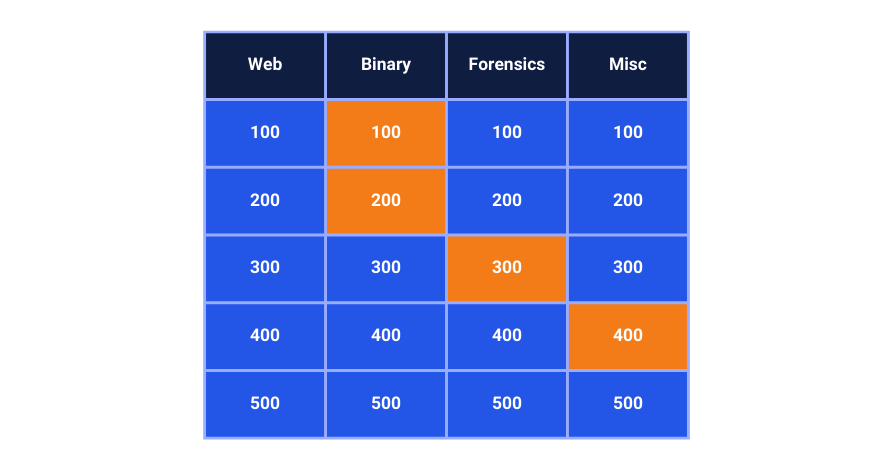
a) Jeopardy-style CTFs
Challenges are organized into categories (e.g., Web Exploitation, Cryptography, Forensics) with varying point values.
Best for accommodating various skill levels and large numbers of participants.
Features:
- Categorized challenges with increasing difficulty
- Immediate feedback on successful solves
- Flexibility in challenge types and topics
Example: picoCTF, a popular online competition for students
Considerations
- Easier to manage and scale
- Allows for a wide range of topics
- Can be time-bound or run continuously
b) Attack-Defense CTFs
Teams are given identical virtual environments to defend while simultaneously attacking other teams’ systems.
Best for simulating real-world scenarios and testing both offensive and defensive skills.
Features:
- Real-time competition with dynamic scoring
- Emphasis on both attack and defense strategies
- Requires robust infrastructure and monitoring
Example: DEFCON CTF, one of the most prestigious competitions
Considerations
- More complex to organize and manage
- Requires significant computational resources
- Offers intense, realistic cybersecurity experience
c) Mixed-format CTFs
Combines elements from different CTF styles, offering a comprehensive experience.
Best for providing a well-rounded challenge that tests various skills.
Features:
- May include Jeopardy-style challenges alongside attack-defense scenarios
- Can incorporate physical security elements or hardware hacking
- Allows for creative and unique challenge designs
Example: HITB GSEC, which includes both Jeopardy and Attack-Defense components
Considerations:
- Requires careful planning to balance different elements
- Can cater to a wide range of interests and skill levels
- May be more challenging to score and manage
For those organizing a CTF for the first time, we suggest starting with a Jeopardy-style format. It’s flexible, scalable, and easy to manage.
As you gain experience, you can dive into more complex formats for future events.
Step 2: Design Engaging Challenges
It’s essential to create a diverse and well-balanced set of challenges. The aim is to engage participants of all skill levels and offer plenty of opportunities for everyone to learn and grow.
Challenge Distribution
- Foundation (40%): Easy challenges for beginners
- Intermediate (40%): Moderately difficult challenges
- Expert (20%): Complex challenges for advanced participants
This distribution ensures that newcomers can build confidence with early successes, while experienced participants are still challenged by the more difficult problems.
Key Considerations for Challenge Design
- Keep it relevant and align challenges with current industry trends and real-world scenarios.
- Provide clear objectives and sufficient context for each challenge.
- Ensure challenges can handle multiple simultaneous attempts without breaking.
- Make sure it’s fair and avoid challenges that require guessing or depend on obscure knowledge.
- Embed educational value by making each challenge teach a specific skill or concept.
Example Challenge Progression (Web Security Track)
-
Beginner Challenge: “HTTP Header Manipulation”
Objective: Modify a specific HTTP header to gain access to a protected page.
Description: “Welcome, agent! Your mission is to access the secret page on our server. Our intelligence suggests that the server is looking for a specific browser. Your task is to convince the server that you’re using the correct browser.”
Hint 1: “Examine the request headers in your browser’s developer tools.”
Hint 2: “The server is checking for a particular User-Agent string.”
Hint 3: “Try setting the User-Agent to ‘CTFBrowser’ in your request.”
Learning Outcome: Understanding HTTP headers and how they can be manipulated for
security testing.
2. Intermediate Challenge: “Blind SQL Injection”
Objective: Extract the admin password from the database using blind SQL injection.
Description: “You’ve discovered a login page that seems vulnerable to SQL injection. However, the page doesn’t display any error messages or direct query results. Can you still find a way to extract the admin’s password?”
Hint 1: “The query is vulnerable, but results aren’t directly visible on the page.”
Hint 2: “Consider using boolean-based injection techniques to extract information bit by bit.”
Hint 3: “The SUBSTRING and ASCII SQL functions may be useful for extracting character data.”
Learning Outcome: Understanding and exploiting blind SQL injection vulnerabilities,
and the importance of proper input validation.
3. Expert Challenge: “Advanced WAF Bypass”
Objective: Bypass a sophisticated Web Application Firewall (WAF) to exploit a hidden SQL injection vulnerability.
Description: “You’ve encountered a heavily protected web application with a WAF that blocks common SQL injection patterns. However, you’re certain that a vulnerability exists. Your task is to craft a payload that bypasses the WAF and exploits the underlying SQL injection flaw.“
Hint 1: “The WAF is blocking obvious SQL injection patterns. Think about obfuscation techniques.”
Hint 2: “Research advanced evasion methods like HTTP parameter pollution or exotic encodings.”
Hint 3: “You might need to combine multiple evasion techniques to succeed.”
Learning Outcome: Advanced WAF evasion techniques, understanding defense-in-depth strategies, and the importance of secure coding practices beyond relying on WAFs.
Step 3: Set Up a Reliable Infrastructure
To make your CTF event a success, having a strong and flexible infrastructure is important.
This means creating secure spaces for the challenges, managing user logins smoothly, and making sure the platform can handle all the participants.
Make it a great experience for everyone!
Key Components of CTF Infrastructure
-
Containerization
Use container technology like Docker to isolate challenges and ensure consistent environments.
Example Dockerfile for a web challenge:
dockerfile
FROM php:7.4-apache
RUN apt-get update && apt-get install -y
libpng-dev
libjpeg-dev
libfreetype6-dev
&& docker-php-ext-configure gd --with-freetype --with-jpeg
&& docker-php-ext-install -j$(nproc) gd pdo pdo_mysql
COPY ./challenge /var/www/html
RUN chown -R www-data:www-data /var/www/html
EXPOSE 80
-
Orchestration
Implement Kubernetes for efficient management and scaling of containerized challenges.
Example Kubernetes Deployment YAML:
yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: web-challenge-cluster
spec:
replicas: 5
selector:
matchLabels:
app: web-challenge
template:
metadata:
labels:
app: web-challenge
spec:
containers:
- name: web-challenge
image: your-registry/web-challenge:latest
resources:
limits:
cpu: "1"
memory: "512Mi"
ports:
- containerPort: 80
3. Network Security
Implement network policies to control traffic between challenges and participants.
Example Network Policy YAML:
yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: web-challenge-network-policy
spec:
podSelector:
matchLabels:
app: web-challenge
policyTypes:
- Ingress
ingress:
- from:
- podSelector:
matchLabels:
access: web-challenge
ports:
- protocol: TCP
port: 80
4. Monitoring and Logging
Implement comprehensive monitoring and logging to detect issues quickly and maintain fairness.
5. Load Balancing
Use load balancers to distribute traffic evenly across challenge instances, ensuring responsiveness.
6. Backup and Recovery
Implement regular backups and have a disaster recovery plan in place to mitigate potential issues.
Infrastructure Considerations
- Ensure the infrastructure can handle peak loads during the competition.
- Protect the CTF platform itself from attacks and ensure fair play.
- Implement redundancy to prevent single points of failure.
- Optimize for low latency to provide a smooth experience for participants.
Step 4: Implement Dynamic Scoring
A well-designed scoring system keeps the competition exciting and encourages continuous participation throughout the event.
Key Aspects of Dynamic Scoring
- Time-based decay
Earlier solves are rewarded with more points.
- Difficulty adjustment
Challenges become worth fewer points as more teams solve them.
- First blood bonus
Extra points for the first team to solve a challenge.
- Category balancing
Ensure that focusing on one category doesn’t give an unfair advantage.
Example Python function for dynamic scoring:
python
def calculate_points(max_points, solve_count, total_teams, elapsed_time, total_time):
solve_factor = 1 - (solve_count / total_teams)
time_factor = 1 - (elapsed_time / total_time)
return int(max_points * solve_factor * time_factor)
# Usage example
points = calculate_points(500, 10, 100, 3600, 86400)
Scoring System Considerations
Ensure the scoring system doesn’t unfairly advantage certain types of challenges or players.
Make the scoring algorithm known to participants to maintain trust and provide transparency. Implement systems to detect and prevent point manipulation or unauthorized collaboration ensuring an anti-cheat environment.
Step 5: Enhance Learning Opportunities Using These Strategies
Provide Post-Solve Learning Modules
After each successful solve, offer a short learning summary to reinforce the key concepts.
Organize a Post-CTF Workshop
- Host a session where top teams share their solutions and approaches.
- Provide in-depth explanations of the most challenging problems.
- Discuss real-world applications of the skills demonstrated in the CTF.
Provide Detailed Write-ups
- Release comprehensive explanations for all challenges within 24 hours of the event’s conclusion.
- Include step-by-step solutions, alternative approaches, and additional learning resources.
Implement a Mentorship Program
- Pair experienced participants with newcomers for guidance during the event.
- Create discussion forums or chat channels for real-time problem-solving assistance.
Offer Pre-CTF Training
- Provide workshops or online resources to help participants prepare for the competition.
- Cover basic tools, techniques, and concepts that will be useful during the CTF.
Conclusion
Creating a successful CTF event requires careful planning, robust infrastructure, engaging challenges, and a focus on educational outcomes.
Follow these steps and continuously refine the process based on participant feedback and you’ll have an exciting cybersecurity competition that contributes to the growth of the cybersecurity community.
Additional Resources
Below you can find additional resources you can use to create engaging, educational, and impactful CTF events that contribute to the growth and development of cybersecurity professionals and enthusiasts alike.
- Popular CTF Platform
- CTFtime: A platform for finding and participating in CTFs
- OWASP Juice Shop: An intentionally vulnerable web application for security training
- PicoCTF: An educational CTF platform with resources for beginners
- CTF Field Guide: A comprehensive guide to CTF competitions
- Awesome CTF: A curated list of CTF frameworks, libraries, resources, and software